Information Security is pleased to announce the following training opportunities for UNT community members:
Don’t Be Like Rick
Sit back and enjoy episodes of the funny Don’t Be Like Rick short TV series. Learn how to protect yourself from different online threats.
The following links go to the episode and select Register Now.
Specific terminology definitions used in the episodes are provided following the links.
Don’t Be Like Rick: King of Passwords
Don’t Be Like Rick: On Social Media
Don’t Be Like Rick: Security Awareness
Technical Terminology
Two-Factor Authentication - Or multi-factor authentication, is an electronic authentication method in which an individual is granted access to an application or website after successfully presenting two or more pieces of evidence to an authentication mechanism.
Pineapple Device - A spoofed internet connection that makes you think you are logging into an establishment's legit free Wi-Fi
OTP - One-time password is a valid password for only one login session or transaction on a computer system or other digital device.
Password Idols
You may be a great singer, but how are you at creating strong passwords? Take a few minutes to play this educational game to learn techniques to make secure and memorable passwords.

Click on one of the following links to be directed to the game and select Register Now.
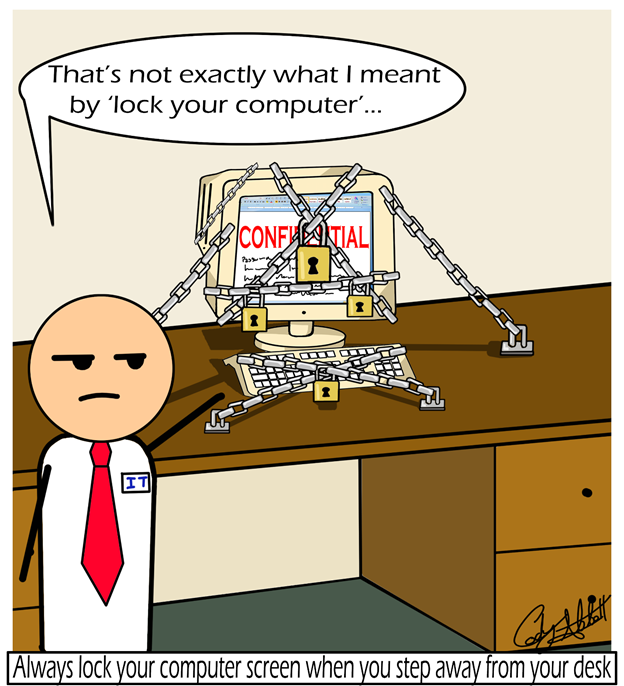
Securing Your Workspace
Physical workspace security is essential. Many employees mistakenly think the only threat from hackers exists online, but protecting your physical environment is just as important to prevent security breaches.
Physical security is the last line of defense for keeping resources and information safe. Follow these tips to ensure your area is always physically secure:
- Always lock your computer screen when you step away from your computer. Using a password-protected screen saver will ensure your computer locks automatically when not in use.
- Keep your desk clear of documents or information that includes confidential information.
- Always lock your office door when you are away.
- Try to ensure no one is looking over your shoulder when you type in a password or access sensitive data.
- Never lend your keys to anyone.
- Never leave valuables unattended.
- Always use a surge protector or a battery backup to protect your computer or device from a power surge. Power surges can result in loss or damage to equipment connected to the device.
- If you notice an unauthorized person in a secure area, report the person to your supervisor or other persons in authority.
How to Choose a Password Wisely and Keep It Safe
An employee’s first defense line against a cyber-attack is often a strong, secure password, but having a complex password isn’t always enough. People tend to use the same password for multiple websites and organizations. However, if one of the websites where they used that password is compromised, all users' personal information becomes compromised. The hacker will have the person’s email address and password for all the websites and organizations used. To avoid this, use a different password for each account.
By following these tips, you can ensure your password is both safe and effective:
- Consider using a passphrase. Build your password from a phrase you already know and can remember. For example, starting with the phrase “Safe and Secure,” you could create “S4f3&s3cur3!” This is both relatively easy to remember and incredibly difficult for an attacker to guess. (NOTE: Please do not use this specific password.)
- Always use passwords that are a minimum of eight characters, including capital and lowercase letters, as well as numbers. Remember – longer passwords are much less likely to be guessed by an attacker!
- Avoid using dictionary words, your EUID, name, or any other identifiable information in your password.
- Never save, write down, or share your password.

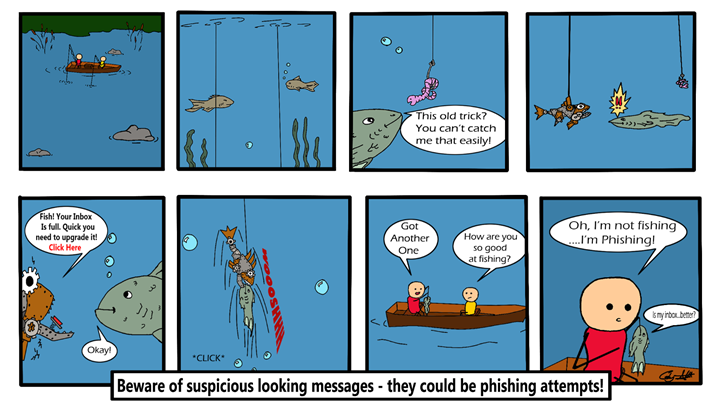
Is This Email a Phish?
One of the first steps to becoming security-aware is recognizing one of the most frequently used tools in an attacker’s toolbox – Phishing.
Phishing is the act of a sender impersonating someone or something through email to get the email’s recipient to click a malicious link or open a malicious file attachment. By doing so, the recipient can inadvertently give an attacker access to and control of employee and organizational information and resources.
Spotting phishing emails is easy to do by remembering a few simple techniques and tips:
- Do not trust any email that urgently requests your personal information, EUID, or password.
- Never click on links in emails until you confirm the sender is authentic. If an email seems suspicious, even though it appears to come from someone you know, consider contacting that person directly to verify that they sent the email.
- Check the From field closely, and know that the From field can be spoofed or faked.
- Be suspicious of emails with links in the body that do not match what is shown in the From email address or the footer.
- Phishing websites may look real using company logos and web addresses that might look similar to the actual web address.
- Always be suspicious of attachments to an email that contains a generic or impersonal message.
- Think twice about any information that an email asks you to provide. Emails from legitimate sources will never ask you to provide or confirm personal or sensitive information through email.
When in doubt, notify UNT System Information Security at security@untsystem.edu of any suspicious email. It is always better to be safe than phished!